Blog
Zeno's Paradox for a Bouncing Ball
2014 Jul 13 01:42 AM UTC | Math7 [2014]3 | Estimated 1-min read
If a ball is thrown up to a height $h$, falls to the ground, and retains a certain fraction $a$ of its energy when it bounces, it will stop bouncing after a certain amount of time. This is paradoxical as it will have bounced an infinite number of times when it stops.
Read more…Uniformly Distributed Tweets
2014 Mar 22 01:49 AM UTC | Math7 Programming18 [2014]3 | Estimated 1-min read
For my Grammar bot, I added a new feature: GPS coordinates are added to the tweets. This is just for fun and serves no practical purpose.
However, I wanted the tweets to be uniformly distributed over a sphere. Earth’s shape is not a sphere, but the error is under 1%.
$a$ and $b$ are random values uniformly distributed in $[-1,1]$
$$latitude=\theta=\sin^{-1}(u)$$
$$longitude=\phi=\pi v=(180^{\circ}) v$$
Buffalo buffalo ...
2014 Mar 6 11:06 PM UTC | English5 Grammar4 Math7 [2014]3 | Estimated 3-min read
Although I have already proven that a repetition of the word ‘buffalo’ $n$ times is grammatically correct, if $n \geq 2$, a year ago, I am now publishing this finding.
- ‘buffalo’ is a plural noun, allowing the use of zero articles
- ‘buffalo’ is also a verb that means to bully, confuse, deceive, or intimidate
Theorem:
Repeating $n$ times, where $n \geq 2$, any word that can be a noun or verb forms a grammatically valid sentence.
Proof:
Read more…Partially Protecting Password Data in Transit
2013 Sep 28 02:39 AM UTC | Security2 Web13 [2013]10 | Estimated 2-min read
HTTP does not encrypt any traffic. Any of the internet routers can see and log your traffic, and your passwords might be compromised if the server does nothing to alleviate this.
On my arcade, my login form requires JavaScript to be more secure, but it is not perfectly secure.
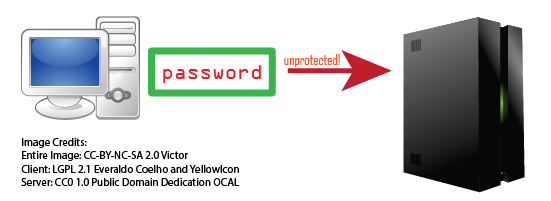 A diagram of the first transmission, unprotected from interception
A diagram of the first transmission, unprotected from interception
The first transmission of the password might be intercepted, which is a vulnerability of this method.
Read more…Python Goto Decorator Improved
2013 Aug 13 11:15 PM UTC | Programming18 Python4 [2013]10 | Estimated 12-min read
When I found a nice hack to get GOTO statements in Python, I decided to make my own version of it. It has been tested on Python 2.7 but probably also works in Python 3.
To use it, import goto from goto and use the @goto decorator:
from goto import goto
@goto
def test():
goto .end
return False
label .end
return True
print test() # should be TrueBut first, you’ll need this code:
goto.py
Read more…Rewriting the Grammar Bot
2013 Aug 8 06:53 PM UTC | English5 Grammar4 Programming18 Python4 Web13 [2013]10 | Estimated 3-min read
I have rewritten my Grammar bot. Previously, it had used regular expressions to find errors, which means that it must check every character against the rules. In addition, Python 2.7 doesn’t support variable-length lookbehinds, which adds extra regular expression checks for some rules. Also, it cannot provide good quotes if there is an overlap between two matches.
Read more…Hacking a Flash Payload Crypter with 1 line of code
2013 Jul 23 05:08 PM UTC | ActionScript2 ActionScript-31 Assembly2 Flash2 Hacks9 Security2 Web13 [2013]10 | Estimated 2-min read
If the flash file puts everything into a binary section and encrypts it, is there any way to decrypt it? If they cut off the header, you won’t be able to memory-dump it, but would you give up there? Of course not!
Somewhere, they have the decrypted data so that they can load it. Just compile some code to intercept it, and inject it:
(new FileReference()).save(_loc_2, "dumped.swf");In RABCDAsm (AS3), it looks like this:
findpropstrict QName(PackageNamespace("flash.net"), "FileReference")
constructprop QName(PackageNamespace("flash.net"), "FileReference"), 0
getlocal2
pushstring "dumped.swf"
callpropvoid QName(PackageNamespace(""), "save"), 2So just put that in the code before it is loaded (call to loadBytes) and replace getlocal2 with whatever will put the decrypted data onto the stack. Once the decrypted data is about to be loaded, you can save it to a file.
In AS2, you’d have to create a server script to echo the file back with FileReference, since it only accepts URL downloads. It’s still feasible though, but writing to a SharedObject and extracting from that might be easier.
In retrospection, I realized that I can also write a fake header if I manage to locate the flash data.
Flasm (ActionScript 2) Bytecode Equivalents
2013 Jul 20 12:55 AM UTC | ActionScript2 ActionScript-21 Assembly2 Flash2 Programming18 Web13 [2013]10 | Estimated 3-min read
Flasm allows people to disassemble flash files (.swf) into human-readable bytecode. I have discovered some of the Flash compiler techniques and other interesting things.
ActionScript // Flasm
Number.POSITIVE_INFINITY // POSITIVE_INFINITY or POSITIVE_INFINITYF
Number.NAN // _NAN or _NANF
return; // push UNDEF / return
trace(x) // push x / trace
// operators: push a / push b / [op]
| // bitwiseOr
^ // bitwiseXor
& // bitwiseAnd
<< // shiftLeft
>> // shiftRight
+ // add
- // subtract
* // multiply
/ // divide
% // moduloWhat I find the most interesting is how it compiles logical expressions:
Read more…